Prism’s Paltry Yield
By Charles Kurzman
June 28, 2013
So now we know what we’ve long assumed: the U.S. government has assembled massive databases of digital communications in its efforts to prevent terrorist attacks. President Obama encouraged debate over the merits of these programs, so let’s start in with an assessment of their effectiveness.
It turns out that they are not very effective at all. Our investment of billions of dollars and degraded liberty has prevented a small proportion of terrorist plots, globally and domestically. So far as we can tell from cases in the United States, there have been no last-minute disruptions of terrorist plots — the scenario that is used to justify these omnivorous databases, end-running America’s time-honored system of narrowly-tailored, court-ordered search warrants.
This sort of informed debate was not possible until Edward Snowden’s leak of documents to The Guardian and the Washington Post, which forced the Obama administration to admit that the Prism program and other NSA databases existed, and to offer a rudimentary accounting of their successes.
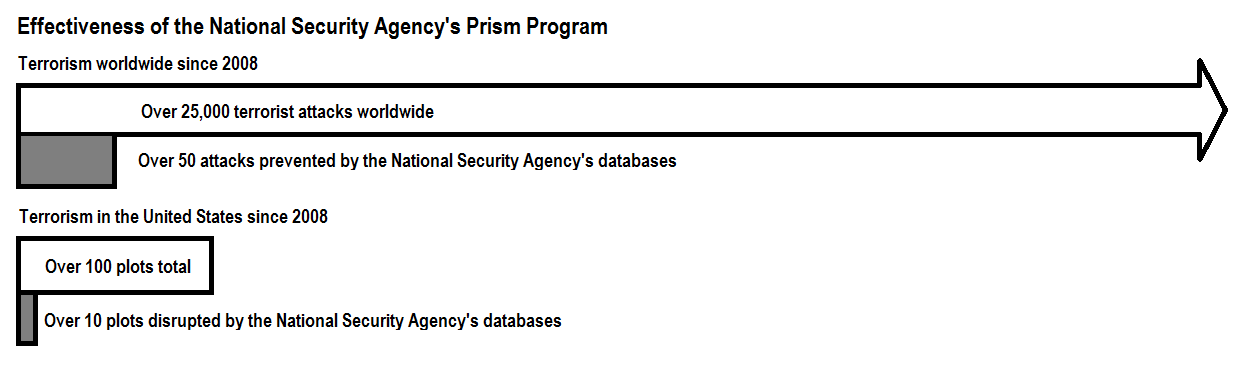
According to General Keith Alexander, director of the National Security Agency, these databases have helped to prevent “over 50 potential terrorist events” around the world, including “at least 10” that involved “homeland-based threats.” “I believe the numbers from those cases, they’re something that we can publicly reveal and all publicly talk about,” Alexander said.
How do these numbers compare with the scale of terrorism since 2008, when the NSA programs were authorized? There have been around 5,000 terrorist attacks each year since then, according to the Global Terrorism Database constructed by the START Center at the University of Maryland. The NSA’s “over 50” disrupted plots constitute one-fifth of 1 percent of this total (see chart).
Domestically, there have been more than 100 “homeland-based” terrorism plots since 2008, two thirds of them focused on joining or financing terrorist groups overseas, according to data that I have collected. (This total includes only plots by Muslim-Americans.) The NSA’s 10 or more disrupted plots constitute approximately 10 percent of this total. Most terrorism plots were uncovered through the usual law enforcement methods: tips from the community, undercover agents and informants, court-approved wire-taps, monitoring open-source social media, and so on.
In other words, the NSA’s unprecedented new powers have not put much of a dent in terrorism. They’ve made even less of a contribution to public safety overall, since terrorism accounts for only 1 percent of fatal violence worldwide, and a fraction of 1 percent in the United States (see chart). (Estimates of deaths due to violence worldwide come from the Global Burden of Disease Study; murders in the United States are tallied by the FBI’s Uniform Crime Report.)
Perhaps the NSA’s 50 disrupted plots were the most dangerous, the largest-scale threats to public safety, and that is why extraordinary data-gathering powers are needed? That’s not the picture we get from the four plots identified by General Alexander and FBI Deputy Director Sean Joyce in their testimony to Congress on June 18:
1. Three Somali-Americans in San Diego convicted of sending about $9,000 to Shabaab militants in Somalia.
2. A used-car dealer in Kansas City who pled guilty to sending about $23,500 to al-Qaeda affiliates in the United Arab Emirates. This case led authorities to two men from Brooklyn who pled guilty to supporting al-Qaeda affiliates in Yemen, including sending tens of thousands of dollars. They were also accused of preliminary reconnaissance of the New York Stock Exchange, though prosecutors labeled this effort “rudimentary and of limited use.”
3. David Headley of Chicago, who pled guilty to conducting reconnaissance for the large-scale terrorist attack in Mumbai, India, in 2008 and a planned attack on a newspaper in Denmark, in conjunction with an al-Qaeda affiliate in Pakistan.
4. Najibullah Zazi, who pled guilty to plotting to bomb the New York subway system after training with al-Qaeda in Pakistan.
The worst violence in these cases was the attack on Mumbai, which killed 155 people, but Prism did not identify Headley in time to disrupt this plot. Federal officials had already interviewed Headley several times in connection with his ex-wife’s allegations that he was active in a Pakistani militant organization, but this investigation did not prevent the Mumbai attack either.
Headley’s Danish plot was still in its early stages when he returned to the attention of U.S. authorities. The FBI’s 38-page criminal complaint against Headley suggests that his telephone conversations began to be monitored in August 2009, when his plot involved only visiting and filming the target sites. The FBI document states that he had made no further progress by the time he was arrested in October, on his way to Pakistan.
The most imminent threat to public safety in these four cases appears to have been the Zazi plot. According to FBI testimony at trial, Zazi was identified as a suspect through e-mail messages he sent to an al-Qaeda affiliate in Pakistan, requesting assistance with the ratio of ingredients for explosives. As several reporters have noted, the e-mail address Zazi wrote to had surfaced during a British terrorism investigation earlier in the year, so the U.S. government may not have needed the NSA’s databases to identify Zazi, only a warrant to monitor the account.
Zazi’s e-mail alerted authorities to his plot on September 6, 2009. The next day, the FBI began surveillance on his home in Colorado. On September 9, Zazi drove to New York, where the plot was taken so seriously that “every terrorism squad in New York City was working on this investigation,” an FBI agent testified. As the FBI knew, because they searched his car, Zazi was not on the verge of an attack — he had left his bomb-making materials back in Colorado, where two relatives were later convicted of disposing the evidence.
Still, General Alexander invoked the specter of a last-minute disruption to justify the NSA’s databases, which allow the agency to search for information on its own computers rather than get a warrant for the technology companies to turn over the information. “The concern is speed in crisis,” Alexander told Congress.
So far, however, I can find no instances of last-minute disruptions by the NSA. Since 2008, three Muslim-American terrorism plots managed to collect weapons or explosives before coming to the attention of law enforcement and being arrested at the last minute. One was arrested in Clarkston, Washington, after posting videos on YouTube about test explosions he had set off; one was arrested in Killeen, Texas, after a gun store clerk called police; and one was arrested in Dearborn, Michigan, after telling a bartender that he planned to bomb a nearby mosque. The NSA’s databases did not help in these cases.
I understand the desire to fight crime with every available tool. The Internal Revenue Services analyzes massive databases to fight tax fraud. The Department of Health and Human Services analyzes massive databases to fight Medicare fraud. But the NSA is not like other government agencies — its budget is secret, its policies are secret, its oversight committee in Congress meets in secret and is sworn to secrecy, and it answers to a separate judicial system whose proceedings and judgments are secret.
Almost all we know about the NSA’s counterterrorism databases is that they have uncovered “over 50” plots in the past five years. Given the scale of violence in the world, that seems like a paltry yield for a program that costs billions of dollars and shrinks our rights to privacy.
Update, July 8, 2013: Apparently some of the NSA’s counterterrorism data-gathering was discontinued in 2011, though other data-gathering appears to continue. If we focus only on the period 2008-2011, the ratios of plot disruption rise to one-quarter of one percent of all terrorism attacks worldwide and one-eighth of terrorism plots in the United States.